The End of the Road: My Final Week at Hack Reactor’s 19-Week Coding Bootcamp
Share
Today marks the last time I will do a week’s review of the Hack Reactor coding BootCamp as I have completed the program and am searching for my first software engineering position. I’ve been focused on an entry-level job since starting my journey as a Software Engineer and into tech in November 2022. This week was a four-day work week in the program, and the last week of the program was for career services. It is focused on handling strategies regarding cover letters, applying for jobs, LinkedIn, portfolio website, the interview process, handling objections, negotiation, alum panel, and upcoming meetings with a career service manager.
Week In Santa Rosa de Cabal, Colombia
During the week, work performing work tasks from 8 am till 6 pm most days with many short walking breaks of 5–15 mins broken up throughout the day and a 45 min lunch at noon. Activities outside of work are having all my meals with the family, walking the dog Almendra and performing pull-ups, and working on my Spanish (this would be talking with locals/family and practicing on Duolingo). On the weekend, we went for a long walk to Finca Recreational Marcelandia, a large hotel that allows you to fish and catch fish for them to cook and then eat for lunch. I have found that this is a popular activity offered throughout Risaralda and neighboring departments. A note on departments as they are similar to what states are in the United States, and Colombia has, at the time of writing, thirty-two departments. In addition, we go as a family (this includes the dog) to church at Parroquia Santa Maria del Monte Carmelo in the town.




Week Work Activities and Learnings
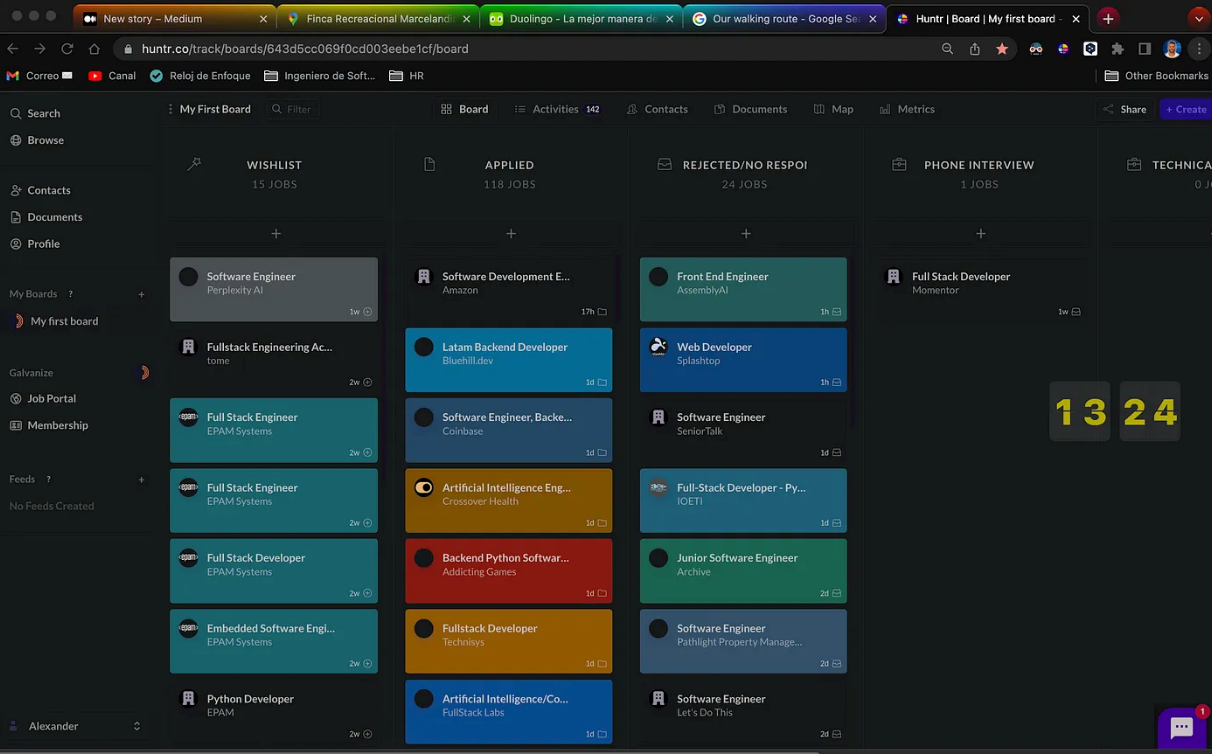
This week I have constructed a template for my cover letter, finished my portfolio website, and have so far applied to 143 positions with 24 rejections and focused on finding openings on the following websites: LinkedIn and Otta. To achieve enough interviews to lead to technical discussions and final offers will take three to six months. I know what to focus on to continue with daily momentum and ensure my mental/physical health is good. I will focus on consistently adding applications to my pipeline, doing my best to send messages on LinkedIn when possible to the listed recruiting team for a position. I plan to spend the first several weeks in full-blown searching 8 hours a day and also making sure I keep my skills sharp by using websites like Pramp for practicing interviews and Hacker Rank for practicing concepts of Data Structure, algorithms, code challenges, and such.
In addition, this week, I have been working on broadening my perspective and learning about an ethical hacker, and getting a deeper understating of how black hat hackers hack systems, scan networks, vulnerability analysis, system hacking, social engineering, and session hijacking, to name some of the topics covered. The following are the courses that I have completed this week from the learning path Become an Ethical Hacker:
Locking down the organization - Ethical Hacking: Introduction to Ethical Hacking Video Tutorial |…
Scouting the target - Linux Video Tutorial | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Scanning Networks Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Enumeration Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Vulnerability Analysis Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: System Hacking Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: The Complete Malware Analysis Process Online Class | LinkedIn Learning, formerly…
Ethical Hacking: Sniffers Online Class | LinkedIn Learning, formerly Lynda.com
Learn about ethical hacking, one of the most desired stills for any IT security professional.
Ethical Hacking: Social Engineering Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Denial of Service Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Session Hijacking Online Class | LinkedIn Learning, formerly Lynda.com
Ethical Hacking: Evading IDS, Firewalls, and Honeypots Online Class | LinkedIn Learning, formerly…
Ethical Hacking: Hacking Web Servers and Web Applications Online Class | LinkedIn Learning…
Recently, I came across an interesting concept known as steganography. It involves hiding a message within an image file by utilizing the least significant bits of each pixel. However, this may create suspicion if the image appears too perfect. I learned about several tools to achieve this technique, such as the following links listed:
OpenPuff - Steganography & Watermarking
xiao-steganography.en.uptodown.com
SSuite Picsel Steganography Encryption
The ethical hacking course is eye-opening, especially comparing the surface size of the web and the dark/deep web. It has given me a better understanding of how web applications work and the potential vulnerabilities in the system. Cybersecurity is an ever-growing field, especially with the widespread use of mobile devices. I want to explore potential security flaws in Apple Vision Pro or Metaverse projects. Recently, my girlfriend shared an article about chatbot accounts being sold on the dark web, which has occurred over the past decade with more and more people living digital lives. The article entitled “100,000 hacked ChatGPT accounts up for sale on the dark web” was written by Graham Cluley, an award-winning cybersecurity keynote speaker who has been involved in the cyber security industry since the 90s. I am excited to continue learning in the technology industry, specifically in cybersecurity, as there is a growing demand for solving problems in this field for numerous businesses.
Lastly, as I’m rewriting this article, I forgot to mention that a completed the LinkedIn Learning course Generative AI: The Evolution of Thoughtful Online Search, which highlights how we are in the early phase of seeing mainstream search engines incorporate Gentetive AI ability and in this course, it was referred to as responsive search functionality.
How finding and sharing information online has evolved - Generative AI: The Evolution of Thoughtful…
I have recently gotten access to the Google search labs. However, I've had access for a little while in time without realizing as most of the time, I'm accessing the web. My IP address is from Colombia, and earlier this week, changing my IP address to the US, I realized I was representing the ability to use the Search Lab functionality to Google. This will present a pivot that many content creators in blogs and websites will need to understand how they will generate traffic to their website from this evolution of mainstream search engines continually adding to the user experience. I read a Medium article by Thomas Smith entitled, I Tried Google’s Generative Search. It Will Change Blogging Forever. highlights what this means for publishers and bloggers and how to adapt. I found this article a good gateway into understanding how online search advancements will create new problems that individuals who are used to the old way of the search will need to solve and fast.
The following week coming up.
I’ll be focusing on daily work for job searching and improving my skills for interview preparation and a side project while also assisting my girlfriend in helping with managing the work of several freelancers for designers to help with producing pitch decks for investors and other marketing materials.
We are excited to be going to Bogota in July for a day and a half and meet with a colleague of my girlfriend, another one of her friends she met from her time living in South Carolina, and also meeting with more members of her family while we get ready to fly to Spain and live in Europe until 2024. I’m excited to go to Bogota as this will be my first time. Thank you for your time in reading, and nos vamos el proximo. Below are my contact details. Ciao!
➡️Website
➡️YouTube
Ready to work with Xander Clemens?
I'd be happy to discuss your project and how we can work together to create unique, fun and engaging content.
Go ahead and click here to be taken to my business service page and see what I can do for you. Book a call with me now. Looking forward to chatting soon!


